Leveraging Simple Yet Effective Statistical Techniques
Research by SAM’s IoT Security Lab
Overview
Recently we investigated an IoT malware attacking QNAP devices on our customer networks. Through inspection of DNS queries we managed to isolate the infected devices and block the control servers of the malware. In this post we detail how we identified the infected devices, what actions were taken and how you can protect yourself too.
QNAP is a company that specializes in network attached storage appliances (NAS). Its products are popular in home and SMB networks. In May 2020 multiple critical vulnerabilities were uncovered in QNAP devices allowing an attacker full remote control of the device. Recently cybersecurity agencies in the US and the UK claimed that a dedicated malware named QSnatch had compromised 62,000 QNAP devices worldwide.
Unfortunately, not much information has been published about the malware from a network perspective, leading us to investigate the situation ourselves. Leveraging data from thousands of QNAP devices to build a behavioral baseline, we have identified a malware infecting multiple devices. It remains to be seen whether it is QSnatch or another malware.
Finding infected devices
Malware of most types, including botnets, ransomware or worms usually “phone home” to some command and control server. This server may collect stolen information, hold encryption keys (for ransomware) or even not exist at all until “D-Day” (for botnets). It was therefore logical to inspect which domains QNAP devices under our monitoring are trying to access.
For each QNAP device, we calculated and plotted how many distinct domains it queries every day.
DNS queries by QNAP devices over 5 days
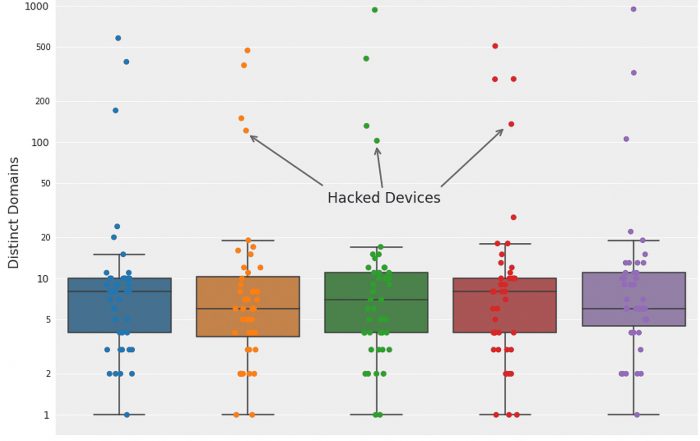
DNS access patterns for 75 QNAPs over a 5 day period. Each point every day, represents a single QNAP device, plotted with the number of distinct DNS queries during that day. The points within the boxes are devices within the “normal” behavior, while the points above are anomalous. This box plot easily reveals the anomalous devices, all found to be hacked.
Most QNAP devices access between 1 and 20 domains daily. These are mainly subdomains under the *.qnap.com and *.myqnapcloud.com umbrellas. However, in the above sample, 4 devices were accessing a significantly higher number of domains daily, as can be seen in the plot (note the logarithmic axis). A deeper inspection found that they are all accessing a large number of randomly generated domains, examples shown in the table below:
Sample of randomly generated domains
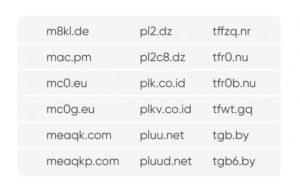
It is important to note that:
- Some of the domains are shared across all infected QNAPs, indicating that it is the same flavour of malware.
- The domains were never queried by any other device which is not a QNAP. This strengthens our belief that it is a targeted QNAP malware.
Identifying the C&C servers
The next step was to understand better the domain access patterns. In a single month, over 300,000 domains were seen. However, deeper analysis uncovers an interesting pattern – most of the domains are accessed once and may be used as “distraction”. Only a small number of domains are accessed more often and by many infected devices.
For each domain we calculated a “rank”, which is simply the number of days it is being queried on. It is shown in the following figure.
Distribution of the suspicious domains
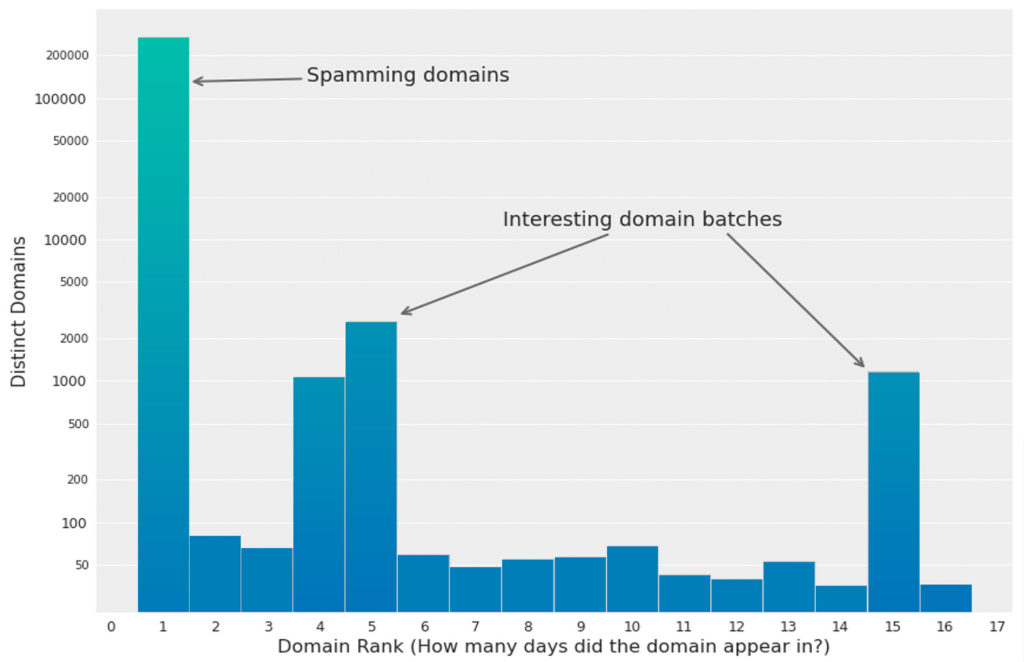
Distribution of the random domains by their “rank”, namely – in how many days is the domain being queried. A huge number of domains are accessed in a single day, never to be seen again. However, two interesting batches of repeating domains stick out.
Some interesting points to take:
- The vast majority of the domains are queried on a single day, never to be queried again. In addition, these domains are accessed mostly by a single QNAP device. It suggests that these domains are “spam” or “distractions” from the real C&C servers.
- A significant “batch” of 2000-3000 domains repeat for 4-5 consecutive days. In addition, they are accessed by almost all of the infected QNAPs.
- Another “batch” of 1000 domains repeat for 15 consecutive days.
If we further inspect the repeating domains, we can clearly see a pattern. These domains rotate exactly every 15 days. They also come in sets of similar prefixes. These domains are accessed by the vast majority of the infected QNAP devices.
We therefore believe that these are the C&C domains.
Timeline of suspicious domain queries
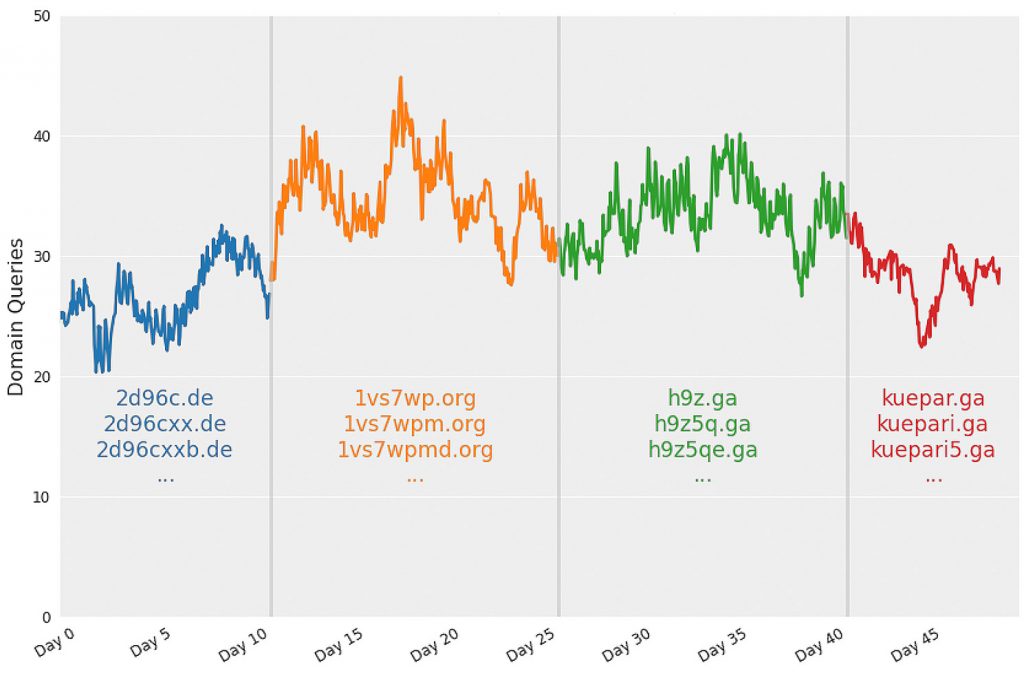
Timeline of the suspicious domain queries, starting from 10th July 2020. The domains come in “sets” with common prefixes. Each set lasts 15 days then disappears, and new ones appear instead (See days 10, 25, 40 in the graph). This clear pattern suggests that these are the C&C servers possibly used by the malware.
Investigating the C&C servers
Most of the domains are not alive. However, a few are. For example, at the time of writing, vxrs47tyqe.vg is alive and running an HTTP server. All domains serve non functional sites, including empty or fake HTTP sites, fake certificates and empty files. This suggests that the malware is currently active.
At that point we believed that we had found the potential C&C servers, and we wanted to block them. Due to the consistent pattern it was rather simple – The domains keep rotating every 15 days. Once they rotate, we can immediately identify the new batch, and add them to a blocking list.
It is left to be understood how the malware infects the devices in the first place. More on that in the next post.
How to protect yourself
Most users will not be able to identify the attack by themselves. However, if you are a power user or a network admin, we can recommend the following actions for detection.
- Monitor the DNS queries of your QNAP devices. In small networks this can be achieved, for example, using Pi-hole.
- The following is a list of legitimate domains accessed by QNAP according to our data. You can whitelist them off the suspicious list. The list may be incomplete if you have installed apps on your QNAP device.
- The following is a list of the latest known malicious domains. If you see any access to one of these, it is highly likely that your device has been compromised.
- If you suspect your device is compromised, either by QSnatch or other, please refer to the official QNAP advisory in order to remove it.
About SAM
SAM’s security platform for home and SMB gateways fingerprints all network devices and applies a behavioral policy to them. It automatically fingerprints QNAP devices and applies a policy, blocking illegal domain accesses and preventing data extraction and DDOS attacks by the mentioned malware. Once we detect an infected device, our customers are notified with a recommended action to remove it.







