Solutions
Partnerships
Delight your subscribers with seamless device management, get to know and understand their usage patterns, and improve your engagement with them using actionable data.

Gain a business advantage by knowing what’s really happening within your subscribers’ networks
Enhance customers’ and employees’ productivity, network management, risk analysis, quality of service, and other home or work experiences with SAM’s automatic discovery, identification, and mapping of network-connected devices.
SAM’s proprietary device fingerprinting solutions, and its ever-expanding database of 100s of millions of identified and monitored devices, allows even the most obscure IoT devices to be identified, and provides you with actionable insights from within the network.

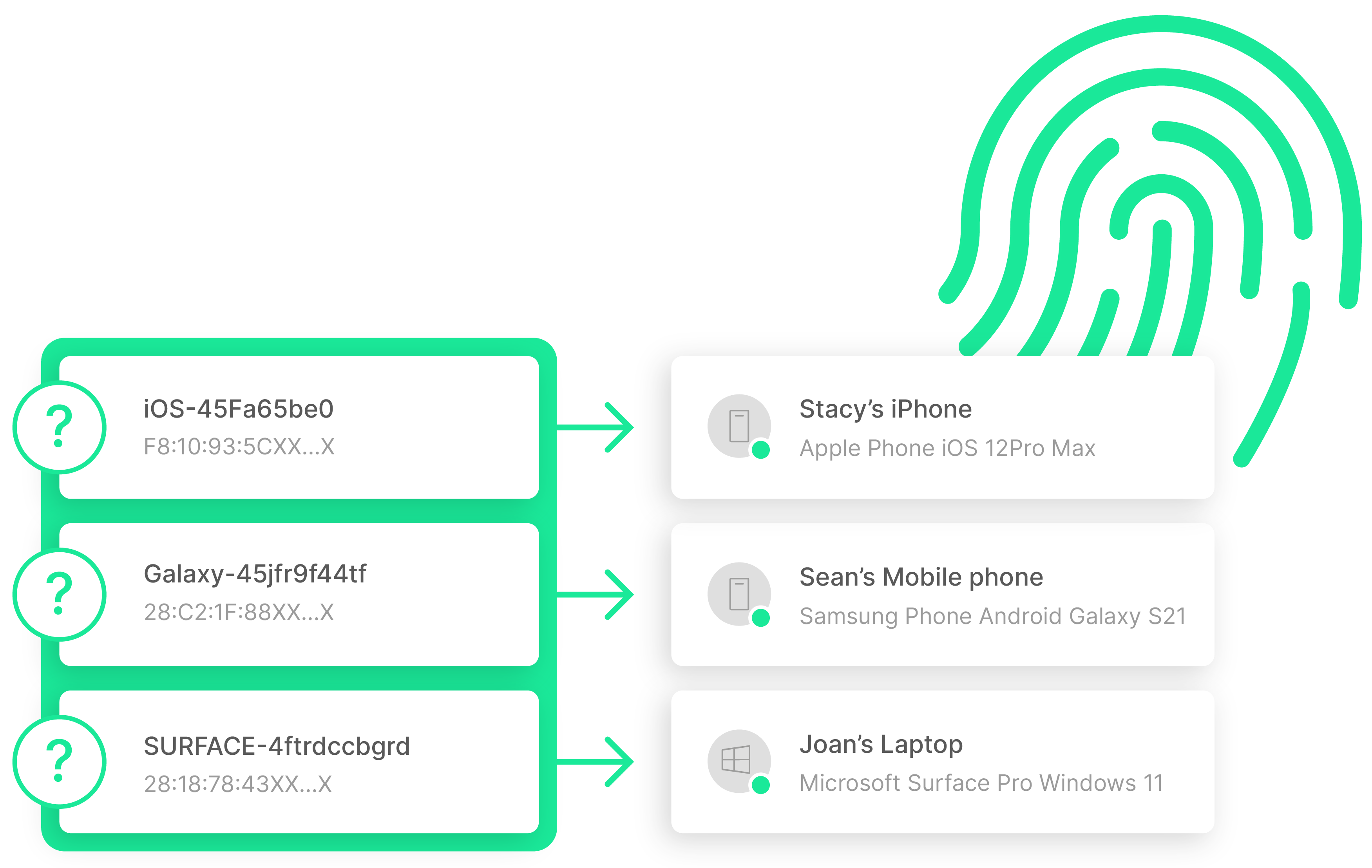
Automatic discovery and mapping of connected devices (including IoTs) utilizing SAM’s device fingerprinting techniques
Identify device manufacturer | device class | device OS | device product name | device model & sub-model
Monitor and alert on new/disconnected/reconnected devices
Offered as a CPE-embedded and/or a mobile app solution
Interested in learning more?
Take a look at our SAM LIGO brochure
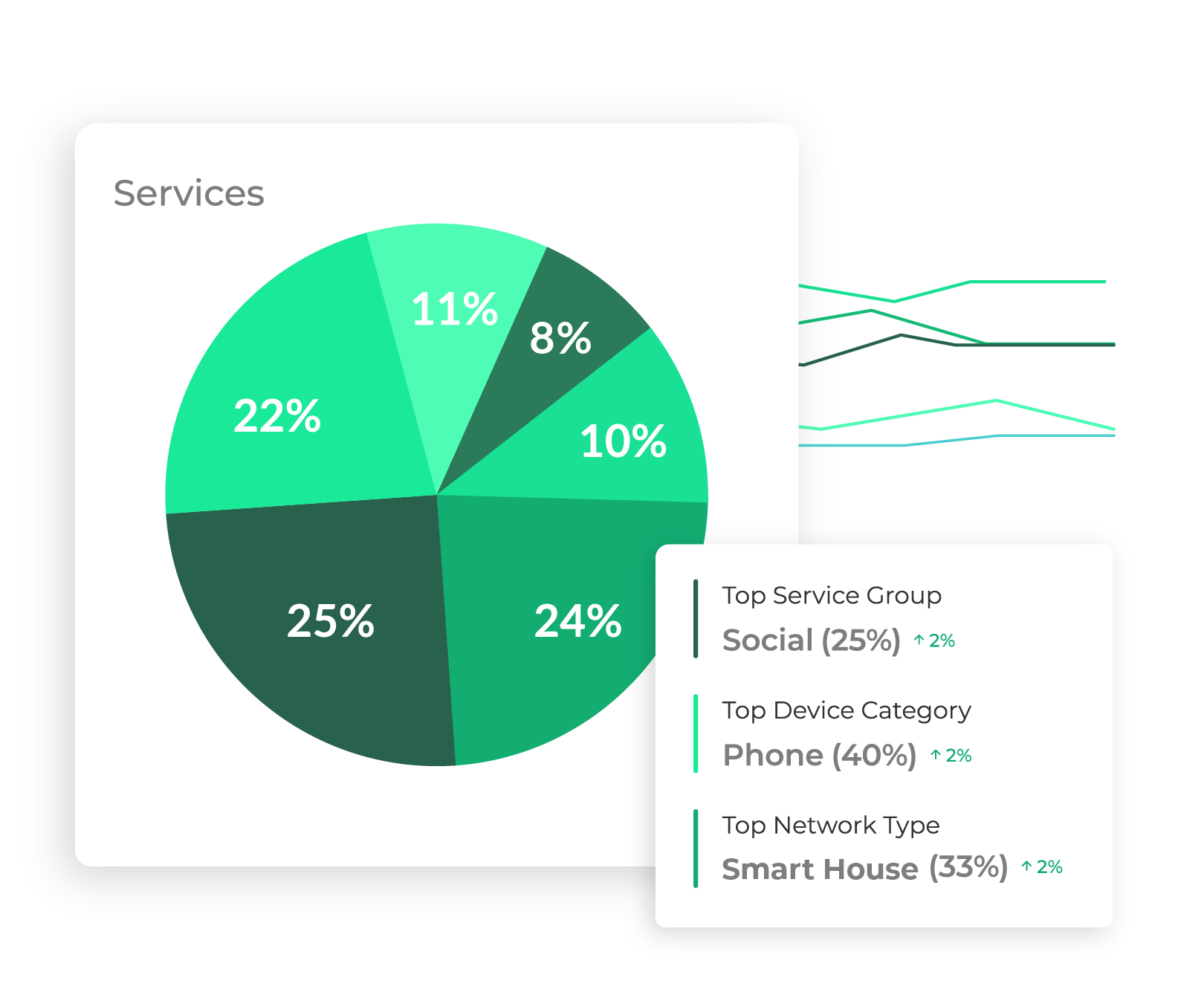
As a complementary service to device identification solution LIGO, SAM’s LUXO provides information and analysis on services being used by network-connected devices.
Is this a gaming-obsessed household? A streaming video fanatic multi-dwelling unit? Are cloud backup services being used in that office? Who’s the mobile service provider for that SMB? Get answers to these questions and others, and leverage data and insights to improve support, marketing, sales, network management, and more.

Discover what your customers, users or employees really use with their network-connected devices (including IoTs)
Analyze ongoing network monitoring to understand usage patterns over time
Get insights on devices’ and services’ usage trends, replacement cycles, brands, uptime, and more
Interested in learning more?
Take a look at our SAM LUXO brochure

of all home devices are
smart devices
devices monitored daily for behavior
changes, new signatures and software
updates
devices already fingerprinted
by SAM
Improving the fingerprint of over
18,000 known device types


