Mobile edge computing (MEC) is an emerging concept introduced to bring cloud services and resources to the user/device proximity and exploring them at the edge of the network. MEC helps to meet the requirements of low latency, location awareness, and mobility support. In this paper, we discuss the cybersecurity aspects of mobile edge computing in the context of the 5G transition and facilitates two dismissions – deliver secure infrastructure and utilizing the technology to create safe digital environments for consumers and machines.
Mobile Edge Security for Consumers
While Telecom Providers had been deploying 5G networks prior to 2020, 2020 was the year that the world was introduced to a hands-on experience with 5G with new smartphones from multiple manufacturers including Samsung and Apple. The iPhone 12 was the first model with support for 5G including both mmWave and Sub-6GHz 5G, the two types of 5G, set records for sales1.
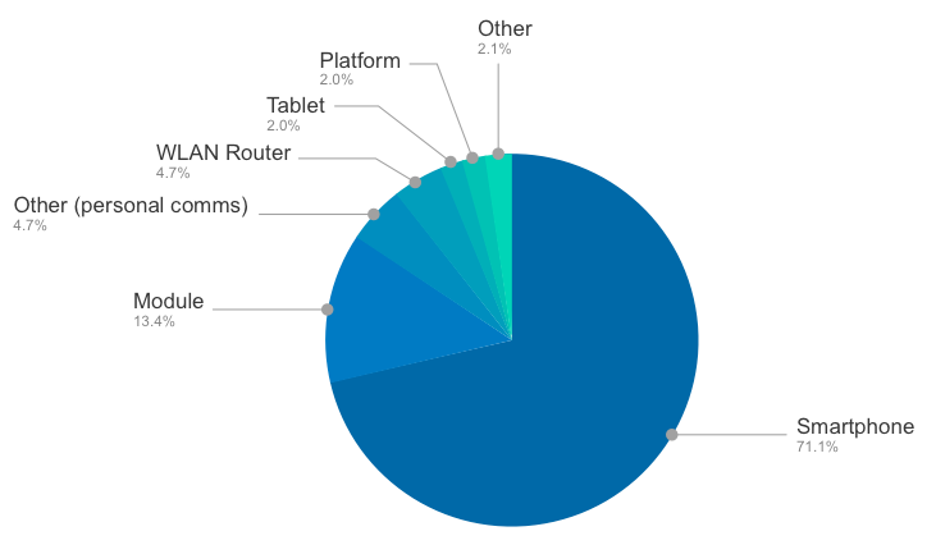
Although you hear the term 5G the first thoughts that come to mind are IoTs, VR and Autonomous Cars; today, smartphones dominate the 5G market. Out of a total of 715 devices which the Global Certification Forum was certified last year, 71.1% were smartphones2, and according to estimates from Ericsson’s latest Mobility Report3, the number of 5G smartphone subscriptions worldwide is expected to rise to 600 million by the end of this year, almost tripling from 2020 in total.
5G Certifications by Type:
Widespread adaption of innovative technology by consumers requires reexamination of both sides:
1) How the technology infrastructure and supply chain should be safe and not increase the attack surface.
2) How we can utilize the technology to protect the subscribers from risks in the application layer.
Safe 5G Infrastructure
The 5G transition enables new services riding on top of 5G brings a tremendous promise. However, invest just in more functionalities, and look at the 5G deployment as a ‘race’ without focusing on securing the infrastructure itself equals leaving the door open.
Rollout 5G deployments, both hardware and software components, require standards that emphasize security and resilience to prevent attempts by threat actors to influence the design, hijack software, or control traffic.
These threats could be prevented by understanding the risks and remediate them before they evolve into a breach:
- Current 5G deployments leverage legacy infrastructure and untrusted components as it builds upon previous generations of wireless networks and is currently being integrated with 4G/3G networks that contain legacy vulnerabilities. Vendors, service providers, and integrators MUST push to upgrade the legacy components, saving money today will cause tremendous costs in the future. According to IBM System Science Institute4, addressing security issues in design is 15 times less expensive than during testing and 100 times cheaper than during maintenance.
- SDN (Software Defined Networking) will play a crucial role in the design of 5G wireless networks. However, like any other software-based solution, ongoing, remote updates are the most considerable advantage and the most challenging risk. Look into similar software-based products; it seems that “The SaaS Application Development Lifecycle” is well defined to handle innovative technology while limiting the possibility of vulnerability in production. However, utilizing the assumption 5G is an isolated network increases the attack surface dramatically. Therefore, vendors, service providers, and integrators MUST adopt secured cloud development methodologies that assume that everyone is accessible, but no one is trusted – Zero Trust.
- The barriers to entry 5G marketplace as an infrastructure provider today are very high; just a few vendors (e.g. Nokia, Ericsson, Samsung and Huawei) are building the core infrastructure, which creates limited competition, resulting in proprietary solutions. The ability of the community to audit proprietary solutions is challenging, so programs like ‘bug-bounty” cannot be fully leveraged. Combining that with the hidden risk of limited competition – once a hacker discovers a vulnerability in one component, it has a worldwide impact – might damages the reputation of the entire 5G industry. Vendors, service providers, and integrators MUST leverage open architectures like O-RAN and OpenRAN.
True Seamless Security
The promise is that 5G will bring speeds of around 10 gigabits per second to your phone. That’s more than 600 times faster than the typical 4G speeds on today’s mobile phones—fast enough to download a 4K high-definition movie in 25 seconds.
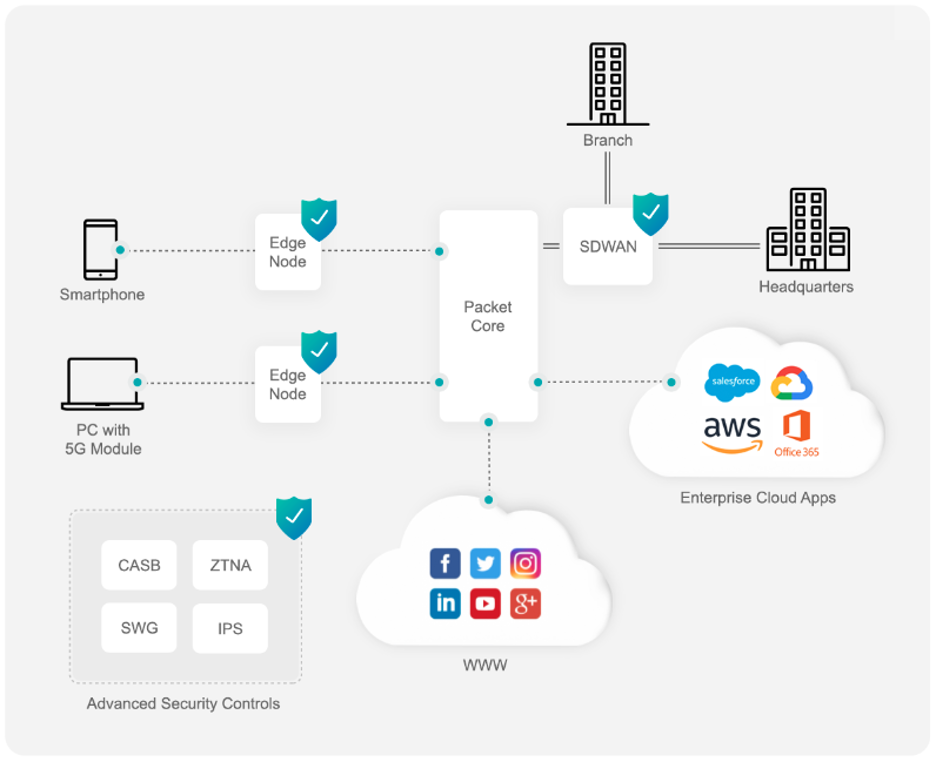
Reaching 10gigbit per second and 1ms latency requires offloading cloud computing into the edge, known as Mobile Edge Computing (MEC). It helps reduce congestion on mobile networks to enhance the quality of experience (QoE), and routing reduces costs which is essential in mass production technologies.
MEC will also change the way consumers are protected. While today, consumers mainly using Endpoint Software like Antivirus to defend themselves. MEC releases the chains of download, install and maintain endpoints software, damages the battery, and requires dedicated flavor for each operation system missing the advantages of Cloud Applications.
Leveraging MEC helps us to change the game in the following areas:
- User Privacy – VPN is a great tool to protect user privacy; it masks IP addresses, so your online actions are virtually untraceable. Even more importantly, VPN services establish secure and encrypted connections. One of the well-known downsides of VPN is the slow internet caused by doubled roundtrip of traffic. Before the mobile device traffic arrives its destiny, it is redirected via the VPN server itself, which might be located far away from the user or the destination. Installing VPN servers closer to the endpoint would increase efficiency and save bandwidth costs.
- Digital Safety – being anonymous is just a part of the equation of information security. Another factor that is even more important is filtering malicious content like malware, phishing, and spyware, which delivers in email, websites, and social media. Today, mobile devices are protected against these scenarios mostly by Endpoint Security Software. However, most of the consumers do not have the awareness required to make it happen. Having a Safe Browsing module in the edge will provide agentless, network-based security that can protect mass production users.
- Remote work – As 5G networks allow users to send large amounts of data to cloud-based applications, it will require the traffic to go directly into the cloud without passing through their organization’s private networks. However, CISOs will want to enforce advanced security controls such as Zero Trust (ZTNA), Cloud brokers (CASB), and Secure Gateways (SWG). Applying these security controls without redirecting the traffic via the organization’s private networks will require an extension of the SASE6 solutions into the Mobile Edge.
Mobile Edge Security for IoTs
Although, the a high adoption rate of 5G by smartphones vs IoT devices today. Billions of dollars are spending on access machines into the mobile network via cutting-edge technologies like eMTC, NB-IoT, NR-Light, and eMBB. Imagine being able to wear smart glasses outdoor, without any WiFi Hotspot around, or text your vehicle to drive itself from the parking garage to pick up your children from the school.
Today, IoT Security solutions are focused on protecting local managed networks such as homes, offices, and enterprises. However, the 5G transition requires IoT security solutions to deep dive into distributed unmanaged assets.
Distributed IoT Security
Unlike enterprise networks, where the CISO or IT team controls which devices can access the network, in the reality of mass production IoT, you need a SIM card to gain access and create damage.
Mass Production IoT Security solution is a cloud-native architecture that leverages the Mobile Edge to identify the devices, enforce security policies and detect anomalies. At the same time, keeping the user privacy safe, not impact the customer experience, and offers the service provider a new way to monetize 5G after investing billions of dollars in the architecture.
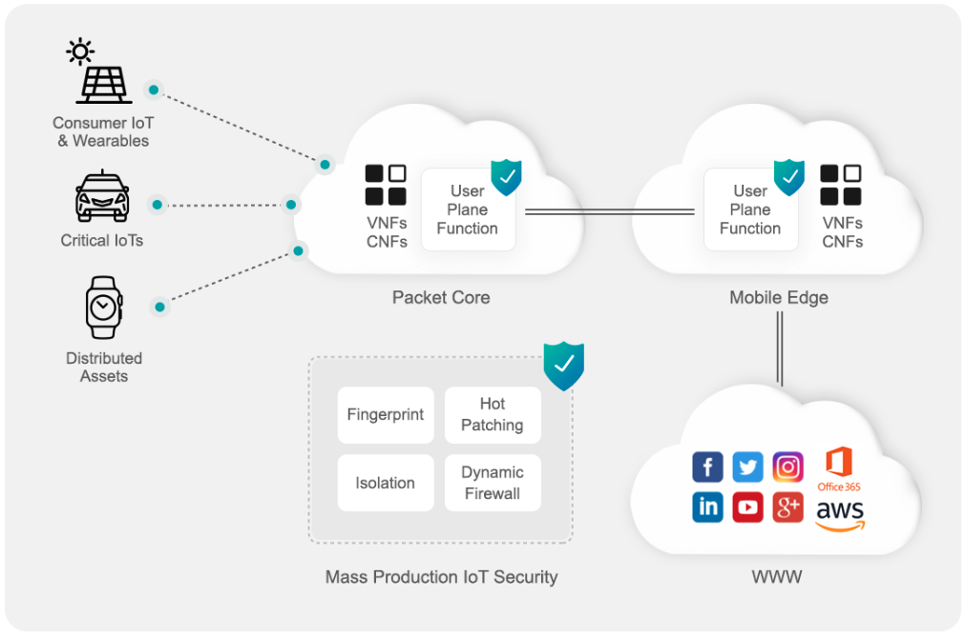
The following technologies are the building blocks of Mass Production IoT Security solutions:
- Device Fingerprint – since the gatekeeper is missing, nobody knows which devices are connected and which vulnerabilities they are entering. Identifying the devices based on their network signature is core functionality that every IoT Security solution should have. The ability to identify devices in seconds up to the specific device model requires leveraging Machine Learning algorithms trained on real-world data sets and being in the edge, so all the required data will be visible.
- Smart Policies – once we identified connected devices, we can enforce smart security policies. It covers both security aspects – prevention & remediation, built on top of two enterprise-grade technologies: (a) Virtual Patching: Mass IoTs are accessible directly to any attacker as they are connected directly into the mobile. Blocking remote exploits delivered over the network that can impact vulnerable devices is a critical technology to reduce the possibility of compromising the device. (b) Dynamic Firewall: Allows IoT devices to communicate only with internet addresses they are supposed to share, leveraging the device classification. For example, based on thousands of Nest Camera devices connected to the Mass IoT Security solution, we can map the communication pattern of each specifically Nest Camera model and enforce it on each one of them.
- Network Isolation – Slicing is the most crucial concept to implement the personalization of mobile networks for unmanaged devices. By the definition of 5G network slicing, logical networks can be virtually represented by a single network. Every network slice will have specific network functions to provide tailored services for different requirements to offer better agility, flexibility, and cost-efficiency. Isolation of each network slice helps service providers and organizations enhance their products’ privacy and security by leveraging it to isolate threats not to impact other network slices. The isolation of network slices implements in various ways, like device classification, risk score, identity, and required functionality.
Make it happen!
While reviewing the paper, I realized how many aspects, just from the security aspects, should be covered and maintained in parallel to all the great opportunities it brings. Enabling 5G is a mission that MUST involve every part of the supply chain, from the physical antenna manufacture to the NFV vendor, which provides VR streams.
Service Providers, vendors, and integrators, we would like to establish reliable 5G connectivity.
References
2) https://www.lightreading.com/5g/5g-device-trends-mmwave-standalone-iot-gain-ground/d/d-id/768307
5) SASE – Coined by Gartner in August 2019, is a new network security model that combines different functions of network and security solutions into a unified cloud security platform to be delivered as a service.







