How do they impact your customers’ quality of experience and how can they help you grow your business?
The IoT ecosystem is exploding and many “smart” homes or small offices have an average of 20 connected IoT devices or more. While anti-virus software protects your customers’ PCs, it does not cover the rest of the network and IoT devices. Therefore, how can telcos help their customers manage and secure all of that and get more for their network investment? What follows is a discussion of two types of approaches, which will help you draw your own conclusion.
It seems like almost anything these days can be connected and become a smart device, even light bulbs or even the bed in which you sleep! What this means is that your customers are connecting a growing number of devices to their routers (“your” routers), which are of course connected to your network. What are these devices and how do they impact your network and your customers’ home networks?
Are they susceptible to hacking and other network intrusions? Can an infected device spread a virus out into the larger, “WAN” network?
And of course, this is a serious issue, as seen in the cyberattack several months ago on a leading ISP, after which the operator had to replace thousands of its customers’ routers.
One way to get a handle on all of this is to create what is called deep network visibility. Of course you know all the main pieces of equipment connected to your network, but it’s time to get deeper and really “scour” all of the end points – and that means thousands and thousands of end points in the form of home and SOHO networks. And there is now a way to implement a relatively simple and straightforward way of realizing this level of clarity, involving network-based solutions that are downloaded and reside in your network.
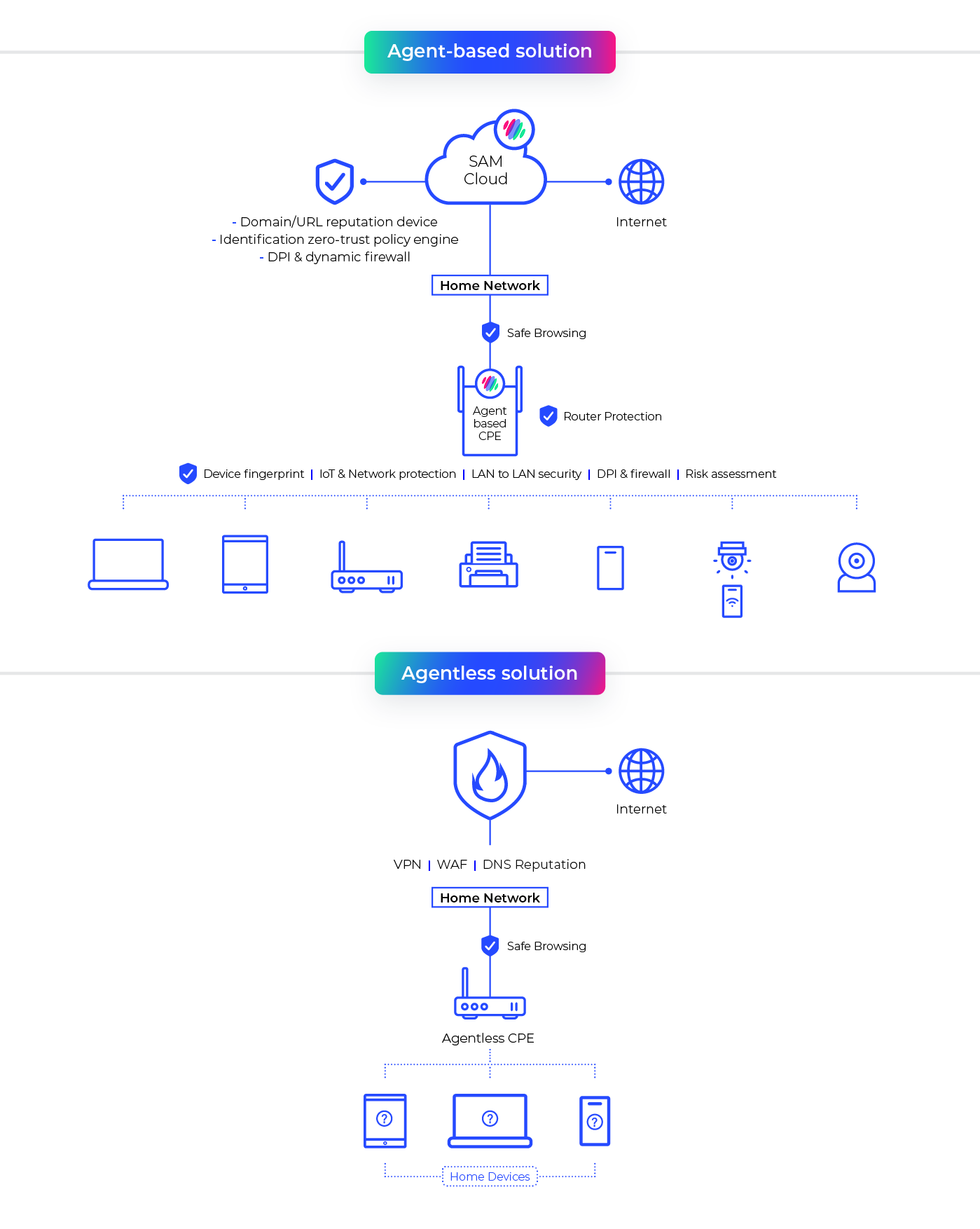
When it comes to ISPs’ networks, there are two varieties of network-based protection, known as “agentless” and “agent-based,” and both provide certain benefits. However, as explained more fully below, an agent-based solution is preferred to achieve true network visibility and protection, and you will reap the benefits of a deeper level of customer engagement as a result.
IOT devices are uniquely vulnerable to cyber-attacks. As described here, IoT devices aren’t built like normal computers. For instance, computers can run programs such as antivirus that are designed to detect and block malware. IoT devices typically do not have enough processing power to support such applications. Furthermore, the IoT ecosystem is very fragmented. For instance, there is an incredibly wide range of operating systems and OEMs, which creates a fragmented approach to security updates – if, indeed, security is even built-in from the beginning – which in most cases is not! Therefore, there is no such thing as downloadable security patches for your kid’s Nintendo and other smart home devices.
Both customers and network operators need “proactive” security at the network level and does achieving deep network visibility automatically result in the necessary level of security? Or does deploying specific security policies, which are based on precise device fingerprint detection the right solution to ensure your network is protected? What type of efforts are required from the operator with each solution and what are the benefits for growing your business? It’s almost a proverbial “chicken or the egg” type scenario and what follows is a discussion of the agentless and agent-based approaches to network security, which will help you draw your own conclusion.
Agent-based solutions – a bit more effort, but a lot to gain!
An agent is a specialized piece of software serving a user or another program that works autonomously and continuously in the user’s program environment – that means it’s actually deployed “onsite” in various locations in a network and act as a localized security mechanism. These agents can be deployed as a network agent over devices such as routers, switches, gateways, and similar equipment. Alternatively, they can serve as an end device agent as a type of antivirus or endpoint protection over supported devices, which include anything from Windows and MacOS clients, virtual machines, and servers to smartphones and tablets.
Agent-based solutions have visibility into all network traffic, which allows them to provide a wide range of security services that benefit both the customer and the network operator, such as: router protection, dynamic firewall, protection against malware and related and full device fingerprinting. And full device fingerprinting is what enables deep network visibility.
The current situation with regards to IoT devices in home environments can be called a form of “digital blindness,” which creates a lack of understanding as to the network topology with connected devices and prevents network operators from effectively managing, supporting and ultimately securing their customers’ networks. Leading agent-based solutions should be based on extensive data sets that fuel the latest AI and ML techniques to achieve the highest level of accuracy, while preserving end-user anonymity, to “fingerprint” every device connected to, for instance, a router or network gateway.
All of this information then creates an environment where service providers are better able to identify and anticipate possible network connectivity issues and increase customer satisfaction. Verizon provides a great example, as the carrier recently deployed an agent-based solution for select customers to simplify and enhance their engagement with these customers and to give these customers a greater sense of control, by removing any doubt as to what is connected to their routers. As a result, these customers are no longer blindsided by unrecognizable devices and activities on their networks.
An agent-based solution then seems like it would be a “no brainer,” but there is some hesitancy to deploy them, so let’s take a look as to why that may be. First, some operators are concerned an agent downloaded onto a customer’s router can affect the user’s experience, as in, it’s another piece of software that could potentially have negative effects on other software or services such as streaming entertainment. However, “thin” field-proven agents have been shown to improve the user experience with a feeling of “hands on” security and greater control over a user’s network.
Another concern is that updating the agent’s software could, frankly, be a “hassle” – causing the router to “go down” at inopportune times, causing customer complaints. Agents today, however, are engineered for “serverless” operations with the code embedded in the firmware. Another issue we hear about is a supposed lack of endpoint visibility, meaning, from the network point of view, looking “towards” the customer, the operator cannot manage all the devices connected to
a router. An agent-based solution actually promotes endpoint integration and protects each managed device from network attacks.
Lastly, there is a misunderstanding that deploying agent-based products is needlessly complex, that it is difficult to account for legacy routers already deployed and new routers deployed as the network expands. To clarify, an agent-based solution does not mean that the Software would be installed on each device (and that the customer would have to do it!). Rather, one agent installed on one router can act as the centralized security authority in that perspective. And it’s important to select an agent-based router-agnostic solution that can also integrate with any end-point solution for mobile or PC – and is not tied to any specific vendor. 2
Agentless solutions – something of a “quick fix”
Unlike agent-based solutions, agentless solutions deploy security by redirecting all traffic through a remote centralized security authority – meaning no software resides in the customer’s home network. Agentless solutions typically redirect traffic towards a VPN or DNS proxy server and some who deploy agentless solutions prefer this scenario as they feel it removes the need to “worry” about the different types of CPE installed at their customer locations. Another way to look at it is an agentless solution is an “outside in” approach, whereas an agent is an “inside out” approach.
Although it has a “zero touch” type of appeal for some customers, the agentless approach does not provide full security for end users, as it is addressing traffic coming from the outside world, but it does not deal with the human error element – such as when someone in the home mistakenly downloads a “bad” file. For instance, if a printer downloaded a malicious file, an agentless solution will not protect against it as it feeds from the outside world and not from data driven from activities from within the home network. Agent-based solutions have that data and can therefore quickly detect anomalies and apply the required remedial policies.
In theory it is feasible to use agent-based and agentless solutions in tandem. But why introduce unneeded complexity into your network operations, when the capabilities of agentless solutions aren’t enough to provide comprehensive security? When relying only on standard endpoint protection or antivirus software, unmanaged devices are left open to vulnerabilities that can potentially harm and infect the network in which they reside.
So now it comes down to the product group’s strategy. If “basic” security is all that is required and minimizing contact (“not bothering”) the customer is a consideration, then the relatively quick to deploy agentless route might suffice. But if a product manager is seeking to differentiate their brand from competitors, increase trust with customers via active engagement, grow ARPU and reduce churn, then the full agent-based solution does indeed become a no-brainer.
A “win-win” scenario
The agent-based path can be implemented as part of a bundling strategy – a way to include security as part of a suite of services to drive ARPU. The story of Bezeq, Israel’s largest ISP, is an excellent example of implementing a swift go-to-market solution that provided an improved home Wi-Fi experience to their customers while simultaneously growing the brand’s ARPU. To significantly differentiate, the carrier launched an effective educational campaign, while positioning their next generation router as stronger, faster, and better looking with security and management capabilities already built in, including one app for all their devices – at home and on the go. It resulted in a 60% penetration rate in three years and corresponding significant revenue growth.
While these strategies could work seamlessly with new home customers, for existing users, the opportunity to upsell their service lies in friction points, such as, moving to a new residence, connectivity issues, support questions, and more. By adopting a security service that gives the ISP complete visibility into their network, it is also possible to efficiently highlight the source of any issues that the customer may be experiencing and use those to upsell.
As for small business customers, they are more aware of threats to their networks. It is important to remember that in order to work with big enterprises they are required to prove that their security is robust and meets a certain standard. The upsell opportunity for low-tier SMBs starts with creating awareness that while anti-virus software protects their PCs, it does not cover the rest of the network and IoT devices. Acknowledge that it may be complicated, but communicate the fact that the process can be automated, so that they can focus on their business instead of IT.
And don’t forget the “feel good” factor. There is something to be said about customers developing a sense of trust with their service provider when they are transparently able to see what it is the ISP is doing for them beyond their connectivity service package. This approach can strengthen relationships with customers and allow an ISP to stand out in the market and stay one step ahead of the competition.