It’s getting more and more simple for IoT attacks to be carried out. The good news? SAM has you covered.
BotenaGo malware has resurfaced. Originally discovered by AT&T Alien Labs in November 2021, this threat has reared its head once more. This time, its source code has been released on GitHub and is available for hackers across the globe to adapt and exploit.
BotenaGo has a total of 33 IoT-related exploits, a list that includes malicious techniques like remote command execution and a telnet loader for the implementation of a backdoor.
“The main function calls together all of the necessary pieces: setting up a backdoor, loading additional payload scripts, initializing exploit functions, and waiting for commands,” writes AT&T Alien Labs. “It is simple and clean malware creation in just 2,891 lines of code.”
What’s more, these vulnerabilities can be found on devices that many of us have in our offices and homes – for example, many of the IoT-related exploits are tied to routers from popular brands including D-Link, Linksys, Netgear, and DASAN Networks.
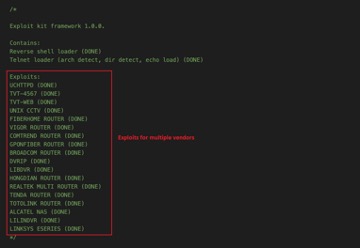
A look at BotenaGo’s exploits for multiple vendors. (Image credit: AT&T)
BotenaGo’s list of exploits isn’t the only issue at hand, though. On top of that, this malicious code couldn’t be easier to access. By publishing the BotenaGo source code on GitHub, it makes it possible for any malicious hacker to use, modify, and upgrade it — or even simply to compile it as a “ready to go” malware script. In other words, it’s getting easier and easier for IoT attacks to be carried out.
Mitigation from SAM’s researchers
Our team has released a new DPI security signature version that covers all IoT-related exploits and we’re actively blocking related attempts with our DPI engine. Our DPI protection is a key element of SAM’s entire defense mechanism that keeps your assets protected.
————————————————————-
Further reading: Multiple attempts to exploit Realtek vulnerabilities discovered by our researchers
————————————————————-
How can you stay safe?
- Maintain minimal exposure to the Internet on Linux servers and IoT devices and use a properly configured firewall.
- Install security and firmware upgrades from vendors, as soon as possible.
- Check your system for unnecessary open ports and suspicious processes.
To make things easier, leaning on the expertise of a skilled security provider can support you in carrying out and maintaining each of the above actions.







